|
By Rezilion
On October 5, 2023, we released a blog post discussing the Curl Vulnerability, the critical security issue in Curl and libcurl version 8.4.0, known as CVE-2023-38545. In addition, there was another low-severity vulnerability, CVE-2023-38546. These vulnerabilities were scheduled to be disclosed on October 11, creating significant anticipation. Now, that long-awaited date has arrived, bringing with it detailed information about the vulnerabilities, along with the release of the necessary patches.
|
By Rezilion
A high-severity cURL vulnerability (CVE-2023-38545) is expected to be published in tandem with the 8.4.0 releases of the package on October 11th. While not much is known about the nature of the vulnerability, according to Daniel Stenberg, Curl’s creator and core maintainer, the vulnerability is “the worst security problem found in curl in a long time”.
|
By Rezilion
By Ofri Ouzan & Yotam Perkal, Rezilion Security Research On September 27th, 2023 Google released an update including 10 security fixes. Notably, one of these fixes, identified as CVE-2023-5217, was highlighted for having an existing exploit in the wild. On October 2nd, 2023, CISA added this vulnerability to their KEV Catalog, signifying that it is being actively exploited in the wild.
|
By Rezilion
For security leaders looking for a more modern approach to improve their application security posture and better manage enterprise risk, enter application security posture management, or ASPM. “Application security posture management analyzes security signals across software development, deployment, and operation to improve visibility, better manage vulnerabilities, and enforce controls, according to Gartner, which is bullish on the technology.
On September 11th, 2023 Google released an emergency security fix for a critical vulnerability discovered, identified as CVE-2023-4863 affecting the Google Chrome for Windows, macOS, and Linux. CVE-2023-4863 is a zero day heap buffer overflow vulnerability in Google Chrome’s WebP with a HIGH 8.8 CVSS score. The vulnerability allows a remote attacker to perform an out-of-bounds memory write via a crafted HTML page.
|
By Rezilion
What exactly does SOC 2 compliance mean? SOC 2 is a voluntary, yet indispensable security standard set out by the American Institute of Certified Public Accountants (AICPA), meticulously crafted for tech companies that hold sensitive data like Rezilion. SOC 2 compliance stands as the pinnacle of data security within the cloud-based products industry and reflects our unwavering commitment to safeguarding our customers’ data privacy and security.
|
By Rezilion
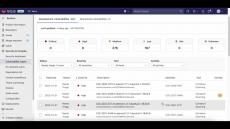
Vulnerability management is difficult and not getting any easier. CISOs and security teams struggle to keep their organizations safe from cyber security threats that come from software flaws. A big part of the challenge is the growing number of vulnerabilities that need to be fixed and the lack of resources available to remediate them.
|
By Rezilion
Application security posture management (ASPM) aims to change the conversation and strategy around software supply chain security. Application portfolios are growing significantly, which is creating headaches for security teams that are responsible for identifying and remediating vulnerabilities flagged in applications. Meanwhile, some of these applications may have been created without IT oversight or awareness, and that only compounds the stress.
|
By Rezilion
Rezilion Named SBOM Vendor in Gartner Hype Cycle for Software Engineering and Representative Vendor for Vulnerability Assessment and Vulnerability Prioritization Technology NEW YORK, Sept. 6, 2023 — Rezilion, an automated software supply chain security platform, today announced that the company has been included in four unique Gartner Hype Cycle reports and identified as a representative vendor in the Gartner “Market Guide for Vulnerability Assessment” report.
|
By Rezilion
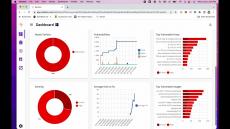
A new Rezilion guide examines the growing trend toward the use of Application Security Posture Management (APSM), which aims to make applications secure and resilient, in turn, significantly reducing business risk. The paper explores the business drivers for ASPM, how ASPM works, what ASPM tools are designed to do, and the benefits of using them. One of the big pain points security teams have is a lack of visibility throughout the continuous development and deployment pipeline.
|
By Rezilion
Azure DevOps is Microsoft’s Software as a Service (SaaS) platform providing developers a comprehensive DevOps platform to develop and deploy software. By integrating directly with Azure DevOps, Rezilion’s platform first helps customers discover all software components in their environment, then using granular run-time validation helps them prioritize vulnerabilities that are exploitable and eliminate what isn’t relevant. This allows developers to focus on what matters most and remediate strategically.
|
By Rezilion
View this video to learn more about Rezilion and CircleCI's integration and see it in action.
|
By Rezilion
Take a deep dive into Rezilion's open source tool, MI-X or Am I Exploitable. Learn what the tool is, what makes it unique, and watch a demo that shows the tool detecting Log4Shell.
|
By Rezilion
Get an in-depth look at Rezilion's Attack Surface Management Platform and how it can reduce your attack surface as well as help manage vulnerabilities.
|
By Rezilion
View a demonstration of Rezilion's integration with GitLab to see how you can reduce patching efforts by 85% so you can code more, release faster, and patch less.
|
By Rezilion
#vulnerabilitymanagement #vulnerabilities #devsecops #devops #sbom #dynamicsbom
|
By Rezilion
Learn how you can fix security issues quickly and easily using Rezilion auto-remediation feature in CI.
|
By Rezilion
Use Rezilion's Dynamic SBOM to create a continuous inventory of all of your software components, map any recognized vulnerability to these components, assess, and share your attack surface.
|
By Rezilion
The recently discovered flaw in Apache’s Log4j software continues to stress security teams and put many organizations at risk. Because Log4j is very difficult to detect, many scanners may not detect it. Rezilion researchers conducted a survey using multiple open source and commercial scanning tools and assessed the tools against a dataset of packaged Java files where Log4j was nested and packaged in various formats. While no scanner was able to detect Log4j in all formats initially, several scanner makers were quick to respond and update their technology to find the bug.
- October 2023 (3)
- September 2023 (7)
- August 2023 (6)
- July 2023 (10)
- June 2023 (11)
- May 2023 (11)
- April 2023 (9)
- March 2023 (11)
- February 2023 (8)
- January 2023 (13)
- December 2022 (9)
- November 2022 (8)
- October 2022 (13)
- September 2022 (13)
- August 2022 (12)
- July 2022 (15)
- June 2022 (20)
- May 2022 (10)
- April 2022 (11)
- March 2022 (9)
- February 2022 (8)
- January 2022 (14)
- December 2021 (16)
- November 2021 (6)
- October 2021 (4)
- September 2021 (5)
- August 2021 (3)
- July 2021 (5)
- June 2021 (2)
- May 2021 (1)
- April 2021 (1)
- March 2021 (1)
- January 2021 (1)
- December 2020 (2)
- September 2020 (1)
- July 2020 (1)
- June 2020 (1)
- March 2020 (1)
- February 2020 (1)
- December 2019 (3)
Rezilion’s autonomous cloud workload protection platform instantly shrinks your attack surface while enabling developers to push code freely.
Rezilion is a stealth mode cyber-security start-up, created by successful serial-entrepreneurs. Rezilion develops a cutting edge technology that makes cloud environments self-protecting and resilient to cyber-attacks.
Security at Cloud Speed and Scale:
- Dynamic Whitelisting & Application Control: By statically analyzing CI/CD pipeline artifacts (code repositories, VM and container images repositories, etc.) Rezilion determines the correct state for every production instance and assures that each is behaving exactly as programmed.
- Hardening & Vulnerability Management: Vulnerabilities, known and unknown, are part of the DevOps life. Unfortunately, they can’t be fixed all at once. Rezilion makes living with vulnerabilities manageable by reducing the vulnerable attack surface — as well as the tension between DevOps and Security teams.
- Exploit Prevention & Memory Protection: Rezilion continuously assesses the integrity of hosts, virtual machines, and containers; providing broad protection against attacks, without the overhead and complexity of legacy solutions.
- Change Control & Access Management: Immutability is a shared goal for developers, IT, and security. However, few production environments are completely immutable. Rezilion helps control and document any manual change that bypasses the CI/CD pipeline.
Effortlessly reduce your attack surface.