Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Detect CVE-2020-8554 using Falco
CVE-2020-8554 is a vulnerability that particularly affects multi-tenant Kubernetes clusters. If a potential attacker can create or edit services and pods, then they may be able to intercept traffic from other pods or nodes in the cluster. An attacker that is able to create a ClusterIP service and set the spec.externalIPs field can intercept traffic to that IP. In addition, an attacker that can patch the status of a LoadBalancer service can set the status.loadBalancer.ingress.ip to similar effect.
How Netskope Can Help with Your 10 Critical Security Projects - Nos. 1-2
The annual list of top security projects from Gartner provides key insights on where security leaders should focus their limited time and resources to be the most effective at protecting their data, users, and infrastructure. Netskope provides value for each of the top 10 recommended security projects for this year and next, including many critical capabilities. This blog series will highlight each Gartner recommendation and how Netskope specifically can help.
Agent vs Agentless Monitoring: Why We Chose Agentless
When we set out to create a cloud-based tool for configuration monitoring, we used the tools we knew and wrote UpGuard using JRuby. For our application, JRuby had many good qualities: getting started only required a one line install, the agent only needed to talk out on port 443, and it was platform agnostic. Using JRuby we demonstrated the value of system visibility, attracted our first cohort of customers, and raised the funds to expand UpGuard.
What SolarWinds teaches us about Zero Trust for mobile endpoints
On December 17, CISA released an alert about an advanced persistent threat (APT) that compromised a number of U.S. government agencies, U.S. technology and accounting companies, and at least one hospital and one university. The cyberattack was executed by injecting malware into a software update from network management software company SolarWinds, which has over 18,000 customers.
Hacking Christmas Gifts: Artie Drawing Robot
If high-tech gadgets are on your holiday shopping list, it is worth taking a moment to think about the particular risks they may bring. Under the wrong circumstances, even an innocuous gift may introduce unexpected vulnerabilities. In this blog series, VERT will be looking at some of the Internet’s best-selling holiday gifts with an eye toward their possible security implications.
CISO Insider S1E2 - "You have unlimited questions left" with Ty Sbano, Part 2
At Nightfall, we believe in the power of learning from those who have done it before. That’s why we created CISO Insider — a podcast interview series that features CISOs and security executives with a broad set of backgrounds, from hyper-growth startups to established enterprises. Through these interviews, we’ll learn how industry experts overcame obstacles, navigated their infosec careers, and created an impact in their organizations.
SDLC Security: It's Personal for JFrog
The SolarWinds hack, which has affected high-profile Fortune 500 companies and large U.S. federal government agencies, has put the spotlight on software development security — a critical issue for the DevOps community and for JFrog. At a fundamental level, if the code released via CI/CD pipelines is unsafe, all other DevOps benefits are for naught.
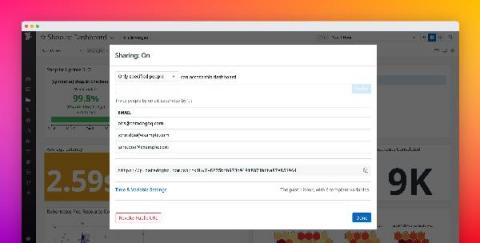
Share Datadog dashboards securely with anyone outside of your organization
Datadog dashboards provide a unified view of your application, infrastructure, and business data, giving stakeholders the context they need to make decisions. Sharing dashboards publicly is useful when you want to make them easily accessible to a large audience. But oftentimes, your dashboards include sensitive information, which is why you need finer-grained controls over the data you share—and who you share it with.
'Tis the season for session hijacking - Here's how to stop it
The air is getting colder, leaves are falling from the trees, and people everywhere are settling in for the holiday season. Which means one thing - increased cybersecurity vulnerability. With more aspects of the winter holidays relegated to online platforms this year, people everywhere are more susceptible to cyberattacks. Luckily, there are plenty of simple steps you can take to protect yourself from digital threats and online scams.