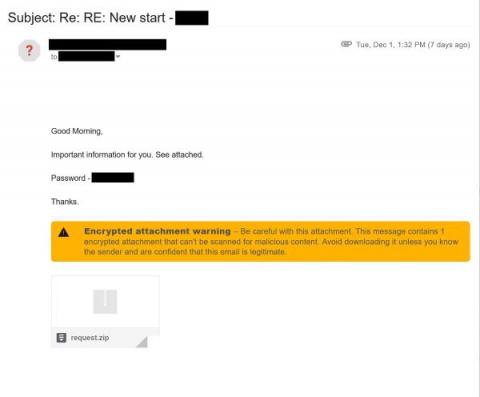
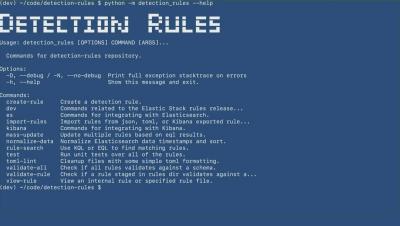
Automation Made Easy: What's New with Splunk Phantom
The Splunk Security Team is excited to share some of the new and enhanced capabilities of Splunk Phantom, Splunk’s security orchestration, automation and response (SOAR) technology. Phantom’s latest update (v4.10) makes automation implementation, operation and scaling easier than ever for your security team.