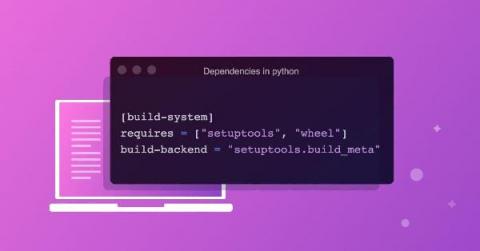
Rezilion Validate in Depth: How We Analyze Python Runtime
At Rezilion, we eliminate friction in the DevSecOps process by identifying which vulnerabilities pose an actual risk to an organization. This dynamic approach allows us to filter out unloaded vulnerabilities and reduce the workload of the security and development teams. Because we need to analyze the process we also need to understand its runtime environment (native, c#, java, python, etc.) and based on its runtime, analyze it differently.