Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Access Management
What is Privileged Access Management (PAM)?
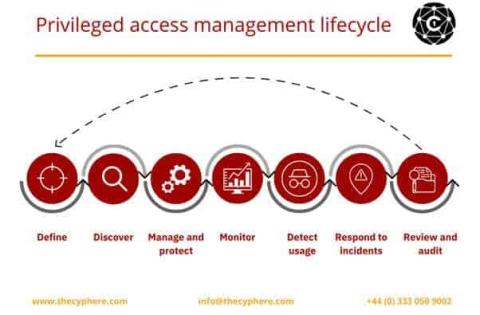
Privileged account management is the process of identifying, controlling and monitoring privileged accounts and their associated activity. Privileged accounts are typically high-level administrator accounts that have broad access rights across an organisation’s IT systems. Because of their elevated level of access, these accounts pose a significant risk if they were to fall into the wrong hands.
SSE: The MVP of The Cybersecurity Mesh Architecture
Overtime IT has adopted a number of siloed security services. These services work adjacent to one another, rather than WITH one another. As you would’ve guessed, this increases complexity and decreases efficiency. This is why we must do away with these types of models. The best security strategies focus on both people and technology. The modern era of work that we are all now experiencing has led to the need for IT security teams to get smarter with every single security incident that occurs.
CIS Control 6: Access Control Management
The Center for Internet Security (CIS) publishes Critical Security Controls that help organization improve cybersecurity. In version 8, Control 6 addresses access control management (in previous versions, this topic was covered by a combination of Control 4 and Control 14).
Things to Ask Your SSE Vendor: Episode 6: Can your SSE simplify access into one UI, agent, & policy?
Privileged Access Management: Essential and Advanced Practices
What is Policy Based Access Management?
We’re excited to be included in the first Policy Based Access Management (PBAM) market report! The KuppingerCole Analysts AG’s 2022 Market Compass provides an excellent overview of how the access market is transforming and emerging vendors in the space.
Stories from the SOC - Lateral movement using default accounts
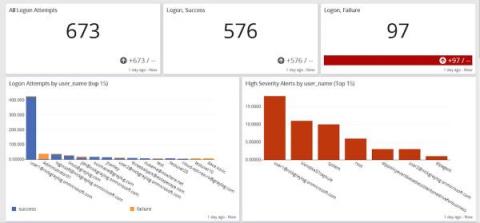
The Windows ‘Administrator’ account is a highly privileged account that is created during a Windows installation by default. If this account is not properly secured, attackers may leverage it to conduct privilege escalation and lateral movement. When this account is used for administrative purposes, it can be difficult to distinguish between legitimate and malicious activity.