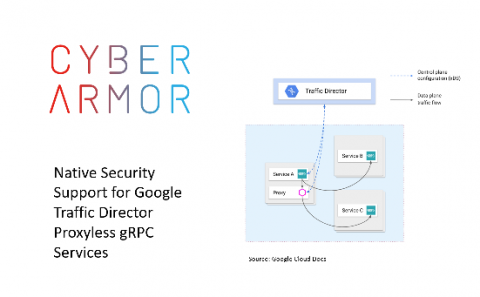
Why Network Peering & Interconnections Matter
In previous blogs on the Netskope NewEdge network, we’ve discussed concepts including Secure Access Service Edge (SASE) architecture and why counting data centers alone is meaningless when trying to understand cloud service coverage. Now that we’ve laid the foundation it seems like a good time to get into what’s needed in terms of architecting the actual network and the connections required.