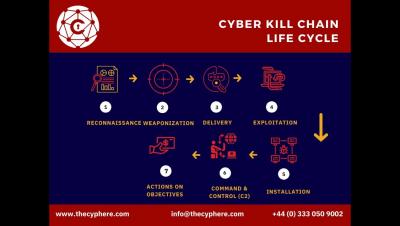
Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Due Care vs. Due Diligence: What's the Difference?
Cybersecurity is more than “just” technology these days. With legislative bodies increasingly writing more laws, technology and legal terminologies have become more intertwined than ever before. As organizations build cyber risk strategies, they need to understand risk mitigation’s underlying goal. This is why understanding the difference between due care and due diligence is important to how you set your risk mitigation strategies.
Bad guys are watching for new openings in your cloud, are you?
You see the headlines, and perhaps, ‘thank goodness it wasn’t us’ flickers through your mind. An overly permissive web server exposes 100 million+ consumer credit applications, or an S3 bucket leaves hundreds of millions of user records open to the public. A nightmare scenario for any CISO and their cloud security team!
Quick Tip // Two-Step Login Verification
WatchGuard Cloud Security Services Help Grow MSP Businesses
Splunk and Zscaler Utilize Data and Zero Trust to Eradicate Threats
SOARing w/ Splunk Phantom
A Look at a Zero Trust Strategy for the Remote Workforce
If you are new to the security world, it is fair to ask yourself, “Isn’t access to data and systems always conditional? Isn’t it always granted to someone who has access to the credentials (ID and password)?” True enough, but in totality, the approach to managing access encompasses a broader spectrum of privacy policies. These policies include a mix of different strategies that can be applied based on an organization’s security vulnerabilities.
Ransomware is the biggest threat, says GCHQ cybersecurity chief
The head of the UK’s National Cyber Security Centre has warned that ransomware has become the biggest threat to British people and businesses. In a speech being given today by Lindy Cameron, chief executive of the NCSC, to the RUSI think tank, she highlights the need for ransomware problem to be taken seriously, and warns of the “cumulative effect” if society fails to properly deal with the rising threat.
5 Risk Mitigation Strategies That Can Save Your Business Lots of Money
Businesses sit on massive, ever-growing piles of data. According to Dave Reinsel, senior vice president, IDC's Global DataSphere, 64.2 zettabytes (ZB) of data was created or replicated in 2020. And the amount of digital data created over the next five years will be greater than twice the amount of data created since the advent of digital storage. But data isn’t just growing, it is spreading to more applications, more users, and more devices than ever.