Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
How Zero Trust architecture improves the organization's network security
In the cybersecurity field, Zero Trust is becoming a widely used model. Data breaches taught organizations to stay cautious regarding security, especially when it comes to information protection - and a Zero Trust model may be the best option. Nobody, including clients inside the firewall, should be trusted, per Zero Trust. Internal threats are a huge concern. And for many attackers, penetrating the barrier is a simple operation, thanks to easy access to leaked credentials.
You can't compare SAST tools using only lists, test suites, and benchmarks
There are a lot of challenges one might face when trying to identify the best SAST tool for your team. But how do you measure something that is meant to find unknowns? How do you know if the tool is appropriate for your needs? How do you compare different tools? It’s no wonder that we often get asked, “Does Snyk Code have coverage for the OWASP Top 10?” followed by “How do you suggest we evaluate and compare different SAST tools?”
Forrester Total Economic Impact of SecurityScorecard Study: Automate - Don't Excel
One of the key reasons SecurityScorecard commissioned Forrester Consulting to conduct a Total Economic Impact™ (TEI) Study was to help the market move on from using spreadsheets as a Vendor Risk Management (VRM) tool. The primary reason for IT teams to look at SecurityScorecard or any other VRM automation platform is simple. IT (Information Technology) will help IT teams get better leverage on their two rarest commodities in the security world, time and talent.
Expecting the Unexpected | How Are Boards Dealing with Threats from Within?
Netskope Named a 2021 Gartner Peer Insights Customers' Choice for Secure Web Gateway
At Netskope, one of our core values as a company is that customers are always our number one priority. We know that technology projects are rarely easy undertakings and it’s our job to be there for our customers and for them to know we have their backs. With that in mind, we are excited to announce that Netskope has been recognized as a Customers’ Choice in the June 2021 Gartner Peer Insights ‘Voice of the Customer’: Secure Web Gateway.
AWS IAM in a layman's terms
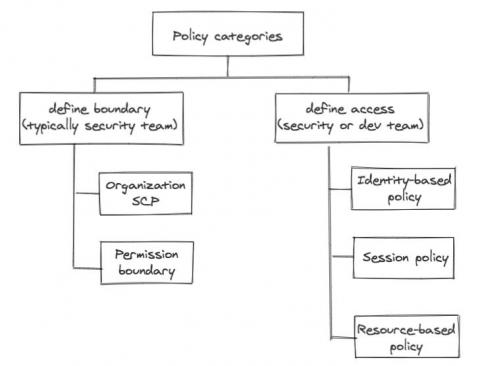
We alluded in one of our previous posts that the development team will own a lot of responsibility defining application related resource access control, simply because the dev team owns the infrastructure as code (IaC) responsibility themselves. No matter how security-savvy and security-educated a development team is, the central security team still needs some control, some kind of “trust but verify”.
Reduce open source risk in M&A with software due diligence | Synopsys
What's New in v8 of the CIS Controls
Back in 2018, the State of Security spent a lot of time going over v7 of the Center for Internet Security’s Critical Security Controls (CIS Controls). We noted at the time how the Center for Internet Security shuffled the order of requirements for many of the existing controls in that version. It also cleaned up the language of the CIS Controls, simplified some working, removed duplicate requirements, and created an abstract for each of the security measures.
What Is a Security Operations Center (SOC)?
Data breaches are costing organizations millions of dollars on average. In its 2020 Cost of a Data Breach Report, IBM found that a data breach cost the average organization $3.86 million. This price tag was even greater for organizations located in the United States and operating in the healthcare industry at $8.64 million and $7.13 million, respectively. What’s behind this price tag, you ask?