Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Veracode Wins Best AppSec Feature Set and Customer Support Awards From TrustRadius
TrustRadius recently awarded Veracode with a 2021 Best Application Security Feature Set Award and Best Application Security Customer Support Award. These honors are given to companies that have gone above and beyond to delight their users. To win the Best Feature Set Award, each nominated organization had to receive 10 TrustRadius reviews in the past year that featured specific mention of their product’s feature set.
Ransomware Gangs Scavenge for Sensitive Data by Targeting Top Executives
In their attempt to extort as much money as quickly as possible out of companies, ransomware gangs know some effective techniques to get the full attention of a firm’s management team. And one of them is to specifically target the sensitive information stored on the computers used by a company’s top executives, in the hope of finding valuable data that can best pressure bosses into approving the payment of a sizeable ransom.
Steps for PCI DSS Gap Analysis
Complying with Standards drawn by the Payment Card Industry Security Standards Council can be complicated and time-consuming. But, with a PCI DSS Gap Analysis, the process becomes a lot easier, streamlined, and less exhaustive. PCI Gap Analysis is the first step towards the Compliance process. The assessment provides details on your current security posture against what is expected and needs to be achieved by the organization.
The Biggest Cyber Attacks and Tips to Build Cyber Resilience
Forrester recognizes Synopsys as a leader in static application security testing
We’re proud to announce that Synopsys has been named a leader in The Forrester Wave™: Static Application Security Testing, Q1 2021. Find out why. This week Forrester recognized Synopsys as a leader in The Forrester Wave™: Static Application Security Testing, Q1 2021, based on its evaluation of Coverity®, our static application security testing (SAST) solution. Forrester evaluated the 12 most significant SAST providers against 28 criteria.
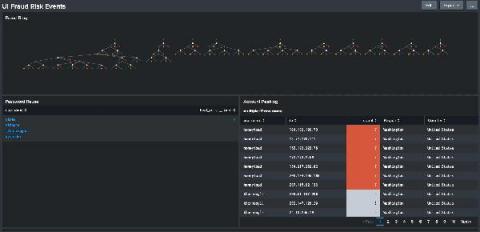
Yes, Virginia, There is a -Santa Claus- Way to Detect Unemployment Fraud
Fraud rates for Unemployment Insurance Benefits (UIB) and Pandemic Unemployment Assistance (PUA) are out of control. In May 2020, Brian Krebs of Krebsonsecurity published two articles detailing fraud that was occurring in several different state’s UIB portals. These states had been warned by the US Secret Service to be on the lookout for this. Reading the articles, the common theme is that many states are missing rudimentary controls for combating fraud.
What is CCPA Data Minimization?
With enhanced information security becoming increasingly more urgent, privacy protection efforts are ramping up for many industries. One of the more recent measures to address data privacy has come from the latest California Consumer Privacy Act (CCPA) Proposition 24, also known as the California Privacy Rights Act of 2020 (CPRA).
What Is the Threshold Application of the CCPA?
When the California Consumer Privacy Act took effect on Jan. 1, 2020, many businesses scrambled to determine whether the law applied to them. The CCPA is the most stringent privacy law enacted in the United States, and for various reasons, its reach can extend well beyond the state’s borders. The objective of the CCPA is to give consumers certain rights to protect their personal data that companies might collect, store, and process for commercial purposes.