Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
How To: Create a Switch Profile in eyeSight 8.3
Hackers Abuse Low-Code Platforms And Turn Them Against Their Owners
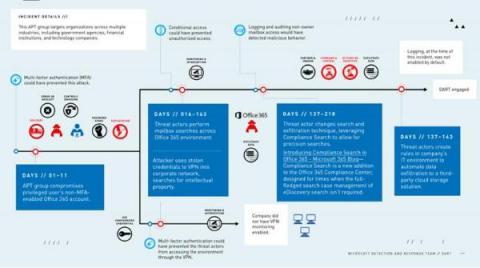
Low-code development platforms open the way for greater independence and efficiency for business users. Unfortunately, they sometimes also open the way for attackers, as a result of poor low-code security practices, especially as low-code application security tries to catch up with traditional application security. Last year, Microsoft’s Detection and Response Team (DART) published the timeline of an attack which leveraged Power Platform, Microsoft's low-code platform.
CISO Dashboard
Cloud Threats Memo: Defining the Latest Dropbox Threat
Who said that cloud services are only exploited by opportunistic cybercriminals? Researchers from Cybereason have recently discovered a new highly targeted campaign, dubbed Operation GhostShell targeting the Aerospace and Telecommunications industries mainly in the Middle East, with additional victims in the U.S., Russia, and Europe.
Optimization is the CISO's COVID Endgame
When the COVID-19 pandemic descended on the U.S., companies took a no-holds-barred approach to maintain their operations. Employees up and down organizational structures were told to work from home, and IT teams were tasked with making that happen. The timeline was short, and approval processes moved quickly, which meant changes to network access and security were made more quickly, and in some cases more haphazardly, than in a “normal” situation.
Privileged Access Management (PAM) with Netwrix Solution
Finding Patterns in the Chaos With User and Entity Behavior Analytics (UEBA)
There’s a great scene in the 1997 film “Contact” where the protagonist Dr. Eleanor Arroway, played by Jodie Foster, is informed that her lab’s funding has just been revoked. Arroway’s lab partner explained that the government lost faith in the project due to concerns of her engaging in questionable activities, such as watching static on TV for hours.
Top 5 Things People Hate About PAM
Privileged access management (PAM) solutions have been around in various forms for decades now. Whether you want a password vault, session management, reduced privilege or a combination of privileged management workflows, there’s been no shortage of vendors to choose from. So why does the thought of PAM still make admins shudder? Surely, it should be enjoyable to have a PAM solution humming along, reducing your organization’s risk while you, the admin, focus on your other duties.
Kubespray 2.17 released with Calico eBPF and WireGuard support
Congratulations to the Kubespray team on the release of 2.17! This release brings support for two of the newer features in Calico: support for the eBPF data plane, and also for WireGuard encryption. Let’s dive into configuring Kubespray to enable these new features.