Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Enterprise Application Risk Profiling
Secure Containers Easily with Base Image Management
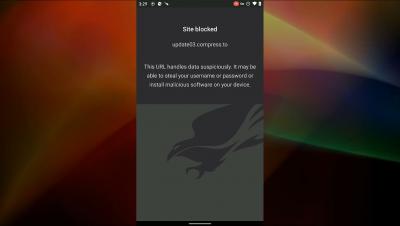
Protecting Users from Malicious Sites with Falcon for Mobile
Citizen Developers Security Awareness
Citizen developers are now producing the types of applications once reserved for professional programmers. By using the low-code/no-code capabilities found in low-code application development platforms (LCAP), business workflow automation or RPA, they can bypass drawn-out development processes and reap the benefits of speed and efficiency. Perhaps even more significant is the resulting efficacy—because who knows better than the citizen developer what the company needs to solve its pain points?
Netskope Cloud Exchange
The Key to Solving Ransomware, Insiders, and Data Theft
The common theme across ransomware, insider threats, and data theft is the exfiltration of data. While threat research labs usually publish the process steps of ransomware encryption, keys, and disk clean-up, the parts about accessing the data and exfiltration are often left out. Also, one security solution does not solve the problem itself, making partner integrations vital to the success of security solution stacks.
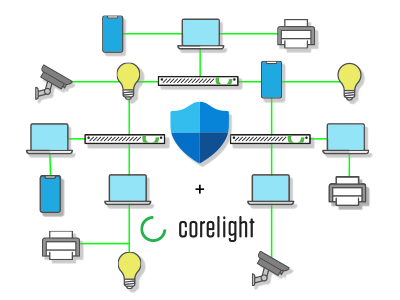
Microsoft + Corelight partner to stop IoT attacks
When you hear the term “Internet of Things,” (IoT) do you picture home devices like lightbulbs, smart assistants, and wifi-connected refrigerators? Perhaps you think of enterprise devices like video conferencing systems, smart sensors, or security cameras? Or maybe traditional office equipment like VoIP phones, printers, and smart TVs come to mind. No matter what devices you imagine, IoT represents an ever-expanding attack surface.