Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
CISO Interview Series: Cybersecurity at a Global Scale
What is it like to not only be a CISO but to also be one in a large, global organization? I recently had the pleasure of speaking with Mark Ruchie, CISO of Entrust, a global tech firm securing data, payments and identities.
What Are the Key Elements of an Effective Risk Management Process?
Risks are a part of everyday life. No matter what decision we take, we always weigh the pros and cons. This core element of our daily lives is risk assessment. When it comes to cybersecurity, risks are omnipresent. Whether it is a bank dealing with financial transactions or medical providers handling the personal data of patients, cybersecurity threats are unavoidable. The only way to efficiently combat these threats is to understand them.
Egnyte Releases Open Source Bandwidth Limiting Plugin
Bandwidth pricing is a major component of the cloud services model. And for a content-heavy service like a video or document store, egress costs can quickly spiral out of control. To mitigate this, it is important to put limits on the amount of data that can be downloaded in a given interval. However, bandwidth limiting for a multi-tenant SaaS product adds a few interesting challenges.
I Left the Founding Team at Uber Eats to Build the Developer Tool I Always Needed
Data stewardship and protection of customer data is likely to become one of the largest challenges for businesses this decade, with a growing number of countries considering data privacy legislation. For example, in 2020, 30 states within the US considered data privacy bills; that number increased to 38 in 2021. This wave of legislation, kicked off by GDPR, started around 2016 when the world entered the Zettabyte era.
Announcing the Nightfall Developer Platform - APIs for Building Data Protection into Any Application
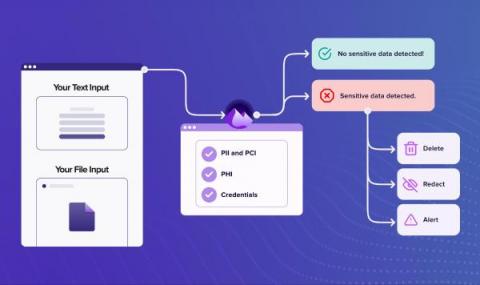
Nightfall’s vision is to power data protection in every app or service. Our native SaaS integrations for apps like Slack, GitHub, and Google Drive already protect organizations, ranging from small startups to the Fortune 100, against data leaks with our machine learning-powered detection engine. Today, we’re excited to announce the launch of the Nightfall Developer Platform, so you can build data discovery, classification, and protection using our powerful APIs.
4 Components of Modern Data Classification & Protection Infrastructure
Data privacy is top of mind for every organization, with individuals wanting reassurance that their data is secure at all times. With the ever increasing number of cloud applications on the market today, security teams are faced with the challenge of keeping track of compounding volumes of sensitive data that can flow internally, externally, and across systems.
Top seven logging and monitoring best practices
Need to build a logging and monitoring solution and unsure where to begin? Get started with our logging and monitoring best practices guide. By: Nivedita Murthy, senior security consultant, and Ashutosh Rana, senior security consultant, at Synopsys.
5 Best Practices for Risk Management
Risk management is the process of identifying, monitoring, and managing potential risks and their negative impacts on a business. These risks can range from data loss, cyberattacks, and security breaches, to system failures and even natural disasters.
October Developer Roll Up
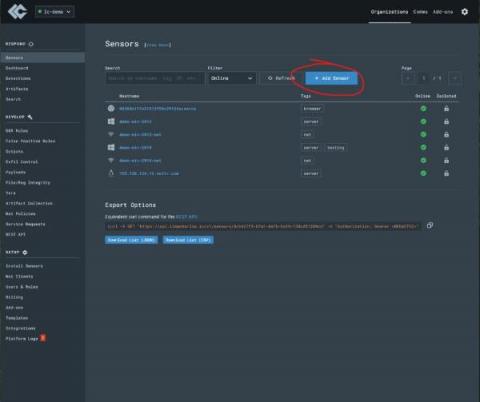
The development roll up this month hints at some of the big improvements we have planned for the web application. Getting new users onto the platform doing the things they came to do quickly and easily is the central theme. LimaCharlie is working to make it easy and intuitive to create the scalable security solutions you need.