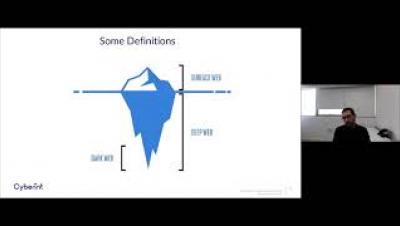
Ping Flood Attacks
The digital world is a vulnerable space prone to attacks of various kinds. Denial of Service is one of the regular strategy attacks used to crash any server. A DoS attack attempts to make a computer or network resource unavailable to its intended users by generating enormous traffic and costing the legitimate users valuable time and money.