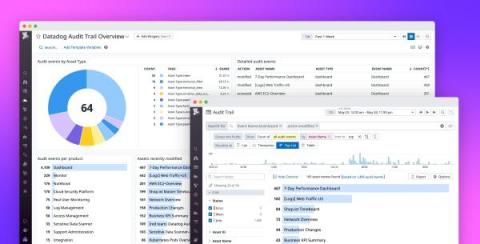
How Should Startups Build Their Tech Stack?
At the beginning of every startup’s journey, the question plaguing every technical founder and their team is how to build their tech stack. A lot of thought must go into this question because it informs how the startup will adapt to the demands of business growth and any necessary adjustments or pivots of the business. In a recent webinar, we discussed this question in detail with Jim Walker of Cockroach Labs.