Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Capture the Flag 101
Springing 4 Shells: The Tale of Two Spring CVEs
The Splunk Threat Research Team (STRT) has been heads-down attempting to understand, simulate, and detect the Spring4Shell attack vector. This post shares detection opportunities STRT found in different stages of successful Spring4Shell exploitation. At the time of writing, there are two publicly known CVEs: CVE-2022-22963, and CVE-2022-22965. The Splunk Security Content below is designed to cover exploitation attempts across both CVEs.
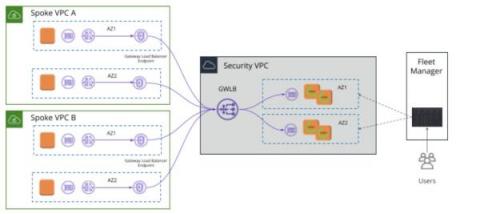
Monitoring AWS networks at scale
Corelight is pleased to announce our integration with AWS’s Traffic Mirroring to Gateway Load Balancer (GWLB) Endpoint as a Target. This integration simplifies the monitoring of network traffic and generating Corelight data in massively scaled-out public cloud environments. When it comes to monitoring network traffic today, we see two primary deployment patterns, each with their own pain points.
SecurityScorecard together with SessionGuardian
Instantly view your organization’s cybersecurity posture + continuously monitor and verify identity.
Identity-Based Data Security on AWS
How to Migrate Your Legacy CurrentWare Software to the New Web Console (2022 Tutorial) | CurrentWare
A Look Back at the Executive Order on Cybersecurity
It has officially been one year since the release of the Biden administration’s Executive Order on Cybersecurity, which outlines security requirements for software vendors selling software to the U.S. government. These requirements include security testing in the development process and a software bill of materials for the open-source libraries in use so that known vulnerabilities are disclosed and able to be tracked in the future, among other things.
This Password Has Appeared in a Data Leak: How to Respond
“This password has appeared in a data leak, putting this account at high risk of compromise. You should change your password immediately” – if you own an iPhone or iPad running on iOS 14 or above, you may have received this worrying message lately. Apple rolled out this feature across both devices and Macs as a cybersecurity feature. If you have received this notification, you might be wondering what it means and what to do next. Read on to learn more.
Impact Analysis: CVE-2022-29218, Allows Unauthorized Takeover of New Gem Versions via Cache Poisoning
It’s been a bad month for RubyGems vulnerabilities. Critical CVE-2022-29176 was issued May 8, 2022, and another critical CVE-2022-29218 was discovered less than a week later, on May 11. This new vulnerability would allow for a takeover of new versions of some platform-specific gems under certain circumstances.