Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
What's new in UpGuard // Cyber Vendor Risk Management Product Releases
Establish an Efficient DLP Policy With These 5 Best Practices
Strong data loss prevention requires two things: a strong policy that guides user actions and permissions, and the tools to monitor and manage data security. Many organizations know they need to invest in software, platforms, and other security settings to create secure networks, endpoints, and cloud settings. But not every organization has a strong DLP policy to guide these tools. Many compliance regimes require companies to record data loss prevention policies.
See Yourself in Cyber: 4 Steps to Stay Safe
As threats to technology and private information become more frequent, the President of the United States and Congress have proclaimed October to be Cybersecurity Awareness Month. This initiative aims to assist people in protecting themselves online. Government and business are working together to increase cybersecurity awareness on a national and worldwide level under the direction of the National Cybersecurity Alliance (NCA) and the Cybersecurity and Infrastructure Security Agency (CISA).
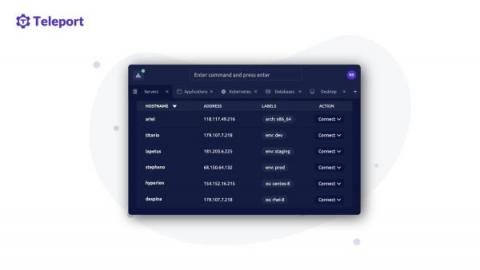
Kubernetes Access support for Teleport Connect
Teleport 10.3 was released on September 30, 2022 along with a lot of new features, bug fixes and improvements. This blog post will focus on one new feature that deserves a deeper dive.
Secure Cloud-native Development: The Top Five Security Pitfalls and How to Avoid Them
The reason organizations are embracing cloud-native development is clear: AWS reports those who migrated saw an average of 20% infrastructure cost savings and 66% increase in administrator productivity. Moving your development process to the cloud offers these benefits and many others, but it also offers a whole new set of security challenges. This series is aimed at helping developers create secure infrastructure for modern, cloud-native applications.
Hack the Box Business CTF 2022: Challenge 1 - PhishTale
Recently, Bulletproof’s pen testers participated in the Hack the Box Business CTF 2022 competition. This was a global InfoSec contest that pitted cyber security teams against one another in a series of hacking challenges, based on real-world vulnerabilities. There were 8 categories which included challenges of varying skill levels for teams to apply their hacking expertise to ‘capture the flag’.