Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Be The Partner of Choice
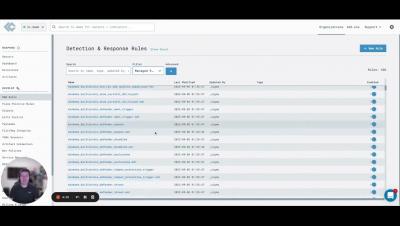
Demo: Policy Audits
Microsoft Exchange On-Prem Zero-Day Vulnerabilities Exploited in the Wild
SOX Compliance Audit Preparation And Checklist
What is FedRAMP?
That’s a good question if you’ve been curious about what it is and if it applies to you. For example, do you have a cloud product that the US Government would gain benefit from using? Are you being asked to seek a security approval or an “ATO” by your customer? We’ll go through the basics of FedRAMP in this article to help you understand where you stand in that process. FedRAMP is a government-wide program.
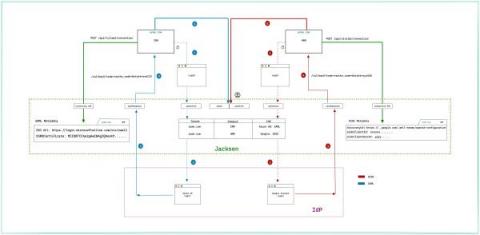
SSO Building blocks - SAML, OAuth 2.0 and OpenID Connect
We have already covered SAML at a high level from both user and application provider points of view. In this post, we'll dive into the technicalities of SAML, OAuth 2.0 and OpenID Connect and how these come together to serve as building blocks for Jackson SSO.
How to Use MITRE ATT&CK to Mitigate API & Other Attacks?
With a threat landscape expanding at an accelerated pace, it is next to impossible for any organization to even keep track of and monitor the volume, frequency, complexity, and breadth of the attack techniques and tactics out there. But to effectively tackle threats and protect mission-critical assets, the knowledge of these common attack techniques, tactics, detection, and mitigation is critical. This is where MITRE ATT&CK is especially useful.
[Part 2] 18 Use Cases for Advanced CAD Data Protection
Reducing the Impact of Ransomware Attacks (Yes, It's Possible)
Ransomware is the fast-growing category of cybercrime. It’s estimated that over 4,000 ransomware attacks occur daily. Given the sheer volume of these attacks and the deep attack surface connections between organizations and their vendors, there’s a high likelihood that some of your employee credentials have already been compromised in a ransomware attack, which means the keys to your corporate network could currently be published on a ransomware gang’s data leak site.