Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Instilling a Higher Level of Trust: Miles & Stockbridge
Instilling a Higher Level of Trust: Miles & Stockbridge
What is VM Replication
2022 Cybersecurity Census Report Unveils Investment Urgency for UK's Education Sector
JUMPSEC works on a prototype lightweight anomaly detection system
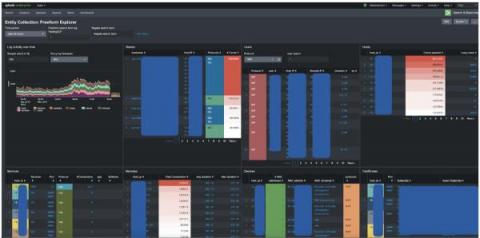
Corelight launches the Entity Collection
Corelight Labs, our amazing research team, has been hard at work on another content collection which we are excited to introduce: the Corelight Entity Collection. Corelight evidence is powerful and comprehensive. So comprehensive, in fact, that it can sometimes be hard to know where to start. Providing customers faster ways to find meaningful context in our data was the driving force behind the creation of the Entity Collection.
A Complete Guide on Comodo EV Code Signing Certificate
EV Code Signing Certificate resides at the top of the digital certificate hierarchy due to its enormous security functionalities. Organizations active for a minimum of three years can only obtain it by undergoing a strict validation process. In addition, Certificate Authorities perform a rigorous verification of all documents before issuing the EV Code Signing Certificate.
How Did Someone Guess My Password?
Finding out that someone has guessed your password can be a scary feeling. Passwords protect your important data, so having someone guess it is a major threat to your security. There are several ways someone could have guessed your password including having bad password habits and easy-to-guess security questions. Read on to learn more about password guessing and the steps you can take to avoid it from happening to your accounts.
2023 Cybersecurity Predictions
In light of the numerous large-scale cyberattacks witnessed in the last year, 2023 promises to be an exciting time for cybersecurity. Outpost24 experts share their thoughts on what we can expect in the new year, and how to best prepare against new threats.