Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
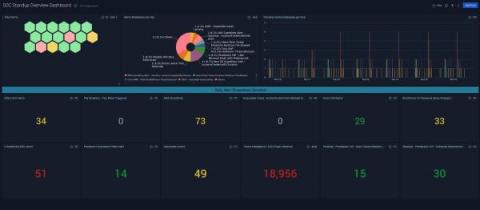
How using Cloud SIEM dashboards and metrics for daily standups improves SOC efficiency
What is SOAR and how does it improve threat detection and remediation?
SOAR (Security Orchestration, Automation and Response) refers to the combination of three different technologies: security orchestration and automation, security incident response platforms (SIRP) and threat intelligence platforms (TIP). SOAR technologies allow organisations to collect and aggregate vast amounts of security data and alerts from a multitude of sources.
How to Run a SAST test: The Dev Tutorial
If you prioritize long-term security and success, you should be analyzing your applications from the inside out. Enter Static Application Security Testing (SAST), a proactive method of identifying and addressing security vulnerabilities in an application’s source code before deployment.
Guidance on network and data flow diagrams for PCI DSS compliance
This is the third blog in the series focused on PCI DSS, written by an AT&T Cybersecurity consultant. See the first blog relating to IAM and PCI DSS here. See the second blog on PCI DSS reporting details to ensure when contracting quarterly CDE tests here. PCI DSS requires that an “entity” have up to date cardholder data (CHD) flow and networking diagrams to show the networks that CHD travels over.
Unified vs API-Based Integrated XDR Platform: What's the difference?
The terms unified and integrated are often used interchangeably in the software world. However, security leaders must understand the differences between deeply unified and API-based integrated platforms within an organization and how they can significantly impact everything from cost to efficiency. First, it is essential to define the terms.
PAN Verification API for the Gaming Industry: What You Need to Know
One of the guiding principles for organisations, whether they are major corporations or small firms, is to ensure compliance. Enforcing compliance helps organisations to adhere to fraud prevention guidelines, identify rule infractions, and shield a corporation from unwarranted penalties and legal action. PAN verification is one such crucial process before onboarding consumers, clients, and third parties in order to remain compliant and within the law.