Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Anyone Can Lose Control Of Their Data
The recent scandal involving Facebook’s data privacy has garnered global media attention and widespread mistrust for the social platform. It all erupted when it was reported that private information from approximately 87 million profiles was used to covertly influence the 2016 U.S. election.
The Severity of Cybersecurity Threats
Across every major news outlet the topic of cyber security threats and data privacy are impossible to miss. From multinational companies being relieved of millions of credit card numbers, to foreign hacking, to the selling of user data via social media, digital security is clearly more important than ever. Threats are being realized by vulnerable organizations large and small.
Securing Your Industrial Network with Tripwire and Belden
Smart Cloud Sessions: How to mitigate risk associated with the Bright Web
Top Facts About Security Operation Centers In Cybersecurity You Need To Know
A Security Operation Center (SOC) can be either a team who works 24/7 in shifts or a facility dedicated and well-organized to detect, prevent, assess, and respond to cyber-threats and incidents and helps to achieve compliance requirements.
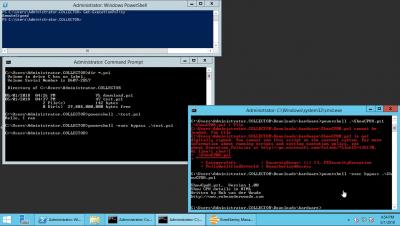
Terminating Malicious PowerShell Scripts
Study: DevOps Servers In The Wild Highlight Infrastructure Security Needs
A mature DevOps practice involves applying multiple tools at different steps of the delivery pipeline, and a new study from IntSights focuses on these tools that may be open to attack on the Internet. Each new tool added to your process can expand your attack surface area – and, in many cases, new development and delivery tools are being used without oversight from a security team.
Endpoint Protection & Artificial Intelligence - Future
Gone are the times when endpoint protection was limited to installing an anti-virus and expecting a reasonable level of protection. With the introduction of Bring Your Own Device (BYOD) and increasing number of IoT devices, there are more endpoints than ever and so are the security threats associated with them.
Best practices for securing your data when terminating an employee
Best practices for securing your data when terminating an employee actually start with the initial onboarding process. Every established organization looking to scale should consult legal counsel after first having drafted an employee handbook. Once created, every employee should be provided an employee handbook outlining the acceptable use policy related to any and all corporate IT resources.