Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Risk Management
Cybersecurity Trends and Predictions for 2022
The 2022 new year is here! That means it’s time to bid farewell to the winter of 2021. At the same time, looking at security trends can give us insight into the future. Last year was a record-breaking year for data breaches. According to the Identity Theft Resource Center (ITRC), the number of publicly reported 2021 breaches in the first three quarters of this year exceeded the total number of incidents in the entirety of 2020.
CMMC 2.0 I L1 & L2 Assessment Guidance
Top Security Risks of Cloud Computing & How to Avoid Them
How to Automate Vendor Risk Management
Protecting Data at Rest vs. Data in Motion
How to Measure Risk Management Performance: KPI & Metrics
Cybersecurity professionals are facing an unprecedented amount of scrutiny. Not only are they responsible for securing and protecting their organizations, but they also need to prove that their ideas and strategies for doing so have a meaningful impact. This can be hard when the threat landscape is constantly changing and new tactics to fight cyberattacks shift regularly.
Manage risks with software due diligence and open source audits
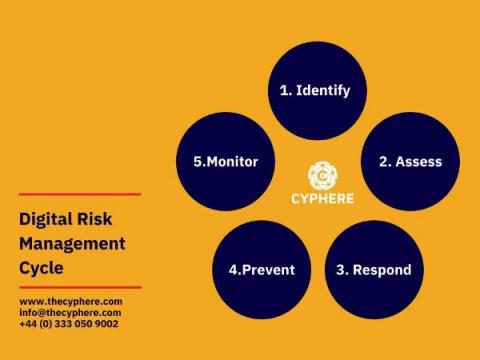
What is Digital Risk? Learn how to Manage it
Digital risks are a big issue for today’s society. Digital risks can be anything from stealing sensitive information to exposing your own personal information to the public. This is why an understanding of the digital risk management process helps businesses to identify and protect themselves.