What is data integrity? Types, examples and how to maintain
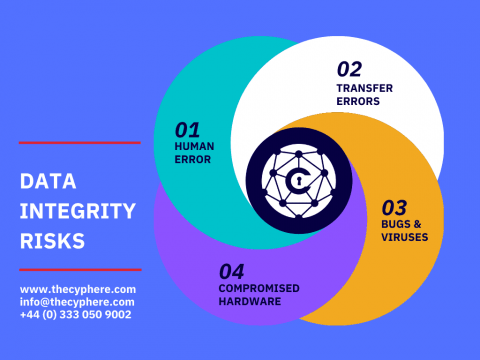
In the present age, when data has become a significant aspect of every business application, more pieces of information have been stored and processed. The security and quality of that information are vital to protect the health of the data throughout its lifecycle. Implementing measures that preserve the integrity of the data is increasingly vital for organisations around the world.