Advanced GDPR Compliance Strategies for Cybersecurity
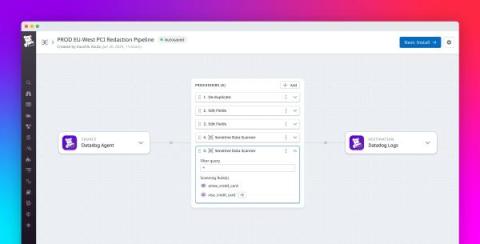
As digital transformation continues to multiply pathways to personal data, complete GDPR compliance is getting harder to attain. Whether you’re a data protection officer or a cybersecurity professional helping your organization remain compliant, this blog suggests advanced GDPR compliance strategies you may not have yet considered - beyond that delightful cookie consent notice we all love.