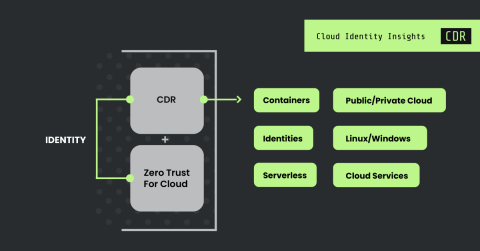
Evolving cloud security: Why identity infused CDR is the key
Minimizing the time to detect, investigate and respond to threats is crucial in stopping cloud attacks. In fact, this might be the biggest understatement in cloud security today. Modern threat actors are escalating their tactics, making attacks faster, more aggressive, and increasingly difficult to stop. Cloud attacks occur at lightning speeds, leveraging automation to access sensitive data and resources before security teams can react.