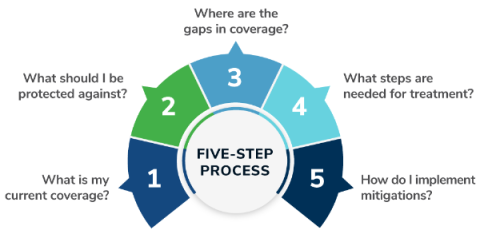
Free Template: MITRE ATT&CK Detection Maturity Assessment & Guide
The threat landscape has evolved rapidly in recent years due to major changes in the way organizations operate and adopt new technologies. Cloud services such as Software-as-a-Service (SaaS) and Infrastructure-as-a-Service (IaaS) have seen massive growth over the last decade. With accelerated digital transformation, increased remote working and cloud adoption, the attack surface has increased for most organizations.