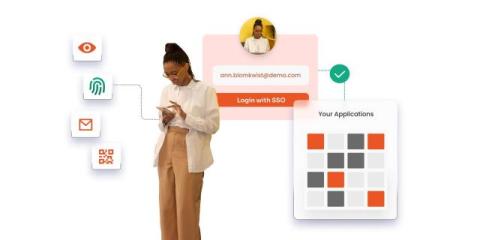
ZTNA is no longer enough. So, what's next?
Remote work. Cloud applications. Mobile devices. They’ve eliminated the days of traditional security perimeters. Today, security must happen at the device level—no matter where that device is. Zero Trust Network Access (ZTNA) earned its place as the G.O.A.T. for remote access—and rightly so. It revolutionized how enterprises secure remote work, but it has its limitations and challenges. UZTNA (Universal Zero Trust Network Access) is the next evolution in zero trust.