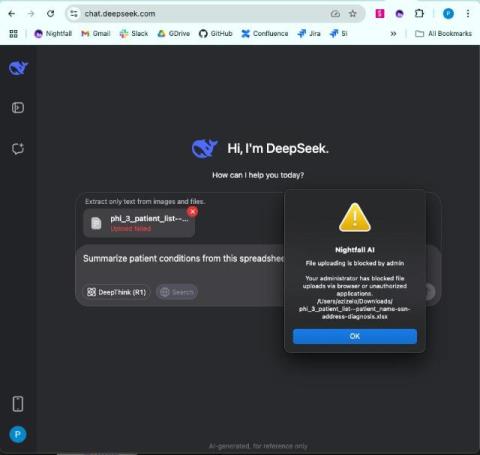
Bridging the Gap Between VMs and Containers
Traditionally, containers and VMs have operated in separate silos, each with distinct management tools and workflows. OpenShift Virtualization breaks down these barriers, allowing VMs to run alongside containerized applications as native Kubernetes resources. This offers organizations the flexibility to modernize their application stacks incrementally, leveraging existing VM-based workloads while embracing the agility of containers.