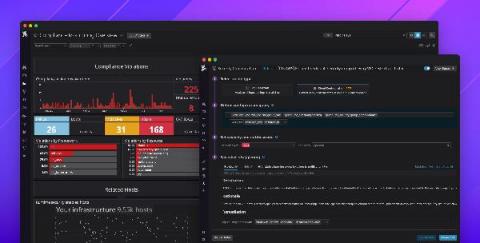
Introducing Datadog Cloud Security Posture Management
Governance, risk, and compliance (GRC) are major inhibitors for organizations moving to the cloud—and for good reason. Cloud environments are complex, and even a single misconfigured security group can result in a serious data breach. In fact, misconfigurations were the leading cause of cloud security breaches in 2020. This puts a lot of pressure on developer and operations teams to properly secure their services and maintain regulatory compliance.