Measure your DevSecOps maturity with Datadog's self-assessment
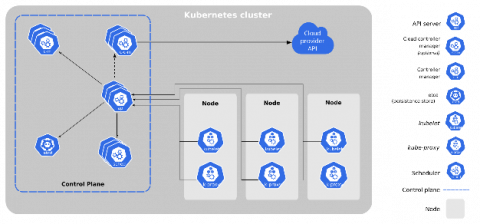
With DevOps teams moving at ever greater speed, it’s vital for security teams to be deeply involved at all stages of the software development and delivery lifecycle. Breaking down silos between development, operations, and security teams ensures that security considerations are not overlooked, that vulnerabilities are caught early, and that security checkpoints do not slow down the delivery process.