Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Market Trends And Predictions For 2022
Sextortion phishing attacks up by 334%
Our threat intelligence have shared several threats they’ve uncovered through monitoring our B2B platform, in our recent report: Keeping pace with emerging threats: Summer 2022 roundup. One of the standout threats to keep your users aware of is a rise in sextortion emails using fake threats to blackmail people into paying cryptocurrency ransoms.
RSAC 2022 round-up: It's good to be back!
The RSA Conference has been a key date on the IT security calendar for 31 years, billing itself as the place ‘where the world talks security’. After being forced into a virtual event last year due to the pandemic, RSAC was back live in 2022 for a face-to-face event at the Moscone Center in San Francisco. This year’s event welcomed around 26,000 attendees, over 600 speakers, and more than 400 exhibitors. So how did a face-to-face RSAC 2022 stack up after the virtual event in 2021?
Massive Interpol Crackdown Nabs 2,000 Alleged Scammers, Intercepts $50M
Read also: security flaw in Travis CI API exposes user access tokens, small botnet launched a record-breaking DDoS attack and more.
What is a Distributed Denial-of-Service (DDoS) attack?
If you don’t work in IT or security, there’s no need to fret about every detail of every online danger. Nevertheless, it’s worth having awareness of the strategies and techniques that criminals are using to achieve their goals online.
A Guide to CIS Control 8: Audit Log Management
CIS Control 8 Center for Internet Security (CIS) version 8 covers audit log management. (In version 7, this topic was covered by Control 6.) This security control details important safeguards for establishing and maintaining audit logs, including their collection, storage, time synchronization, retention and review. Two types of logs are independently configured during system implementation.
A Guide to CIS Control 10: Malware Defenses
Control 10 of CIS Critical Security Controls version 8 is focused on malware defenses. It describes safeguards to prevent or control the installation, spread and execution of malicious applications, code and scripts on enterprise assets. (In CIS version 7, this topic was covered by Control 8.) Malware, especially ransomware, has become a pressing security issue in recent years.
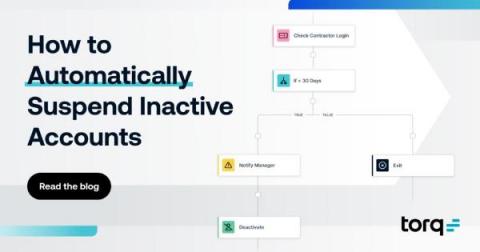
How to Automatically Suspend Inactive Accounts Using Torq
Contractors, freelancers, and other temporary workers have become essential parts of the modern enterprise. For IT and security teams, these individuals present unique challenges compared to full-time workers—and potential risks. The ‘offboarding’ process for these contractors is often less formal than bringing them on. Meaning, many just stop using their entitlements and accounts without actually closing them. These dormant accounts can pose serious risks to the organization.