Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Cyberthreat Defense Report 2022: Key Points You Should Know
Each year, CyberEdge publishes the Cyberthreat Defense Report (CDR). Aimed at IT security leaders, this comprehensive report outlines the threats, security issues, and industry concerns that are most pressing. Information summarized in the CDR is gathered through surveys conducted in 17 countries and 19 industries. Respondents are IT decision-makers in organizations with at least 500 employees.
Reexamining the "5 Laws of Cybersecurity"
Nearly a year ago, journalist Martin Banks codified “Five Laws of Cybersecurity”. Cybersecurity is a complicated field, and any way to simplify its many facets into short, easy-to-remember maxims is always welcome. The five laws are a very good start towards developing a robust security program. The laws are: Of course, compliance with real rules does not necessarily equal security, but these general cybersecurity “laws” are a useful reference.
What Is a Password Manager?
Password managers are tools that provide users and businesses the ability to track, store, protect, share and manage passwords for applications and online services.
How to decide what to fix when you can't fix everything
How to stop sophisticated ransomware attacks
The number and frequency of ransomware cyberattacks are growing every year. The European Union Agency for Cybersecurity (ENISA) recorded a 150% increase in 2020 alone and, as of last year, ransomware attacks have become the number one threat. Added to this, the recovery costs and downtime incurred can be up to 10 to 15 times higher than the ransom demanded by cybercriminals.
Weekly Cyber Security News 17/06/2022
A selection of this week’s more interesting vulnerability disclosures and cyber security news. For a daily selection see our twitter feed at #ionCube24. Anker are a very popular consumer technology company, so if you have one of their home hubs, you might want to take a look pretty quickly.
The Importance of White-Box Testing: A Dive into CVE-2022-21662
I want to take some time to explain the importance of using a white-box approach when testing applications for vulnerabilities. To help in this endeavor, I will use a real-world example to demonstrate how researchers (in this case Karim El Ouerghemmi and Simon Scannell) *may* have found a vulnerability in WordPress (CVE-2022-21662 a 2nd order stored XSS) and how you, as a security researcher, can also use a white-box approach to find an exotic XSS vulnerability.
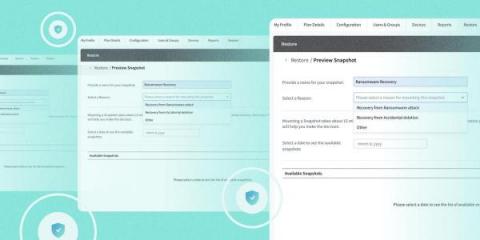
How Egnyte Built Snapshot Recovery to Mitigate Ransomware Attacks
As companies accumulate and store large amounts of business data in the cloud, data security and governance become a major concern. More than 16,000 companies use Egnyte to manage, secure, and govern their content. These businesses rely on the unified platform to keep their business running smoothly, because data loss due to ransomware attacks or accidental file deletion could have profound impacts on their bottom lines.
New in Cybersecurity - Insights, threat trends, & RSA learnings
AT&T Business’ most recently #BizTalks Twitter Chat—What’s New in Cybersecurity—Insights, Threat Trends, & RSA Learnings—explored many emerging concepts in the cybersecurity industry. Head to the @ATTBusiness Twitter page—go.att.com/twchat—to see the full chat and learn more. It was an interesting conversation with diverse opinions. Here are some of the highlights.