Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Citrix's Corey Hill: How to make mental health a priority for your security team
In our latest episode of the Future of Security Operations podcast, Thomas speaks to Corey Hill, Director of Security Operations and Incident Response at Citrix. After working at organizations such as Mandiant and Cisco, Corey joined Citrix in 2020 when there were just a handful of people on the SOC team.
How to Keep Your Data Secure as a Digital Nomad
Now that remote work has become the norm, employees are taking advantage of this opportunity to travel the globe and work from anywhere in the world—as long as it’s within company policy. With the rise of digital nomads, it is important that you know how to keep yourself safe from cyberattacks when working remotely from city to city. This blog will help you understand what you need to do to secure your data as a digital nomad.
JFrog's Advanced Security Scanners Discovered Thousands of Publicly Exposed API Tokens - And They're Active
The JFrog Security Research team released the findings of a recent investigation wherein they uncovered thousands of publicly exposed, active API tokens. This was accomplished while the team tested the new Secrets Detection feature in the company’s JFrog Advanced Security solution, part of JFrog Xray.
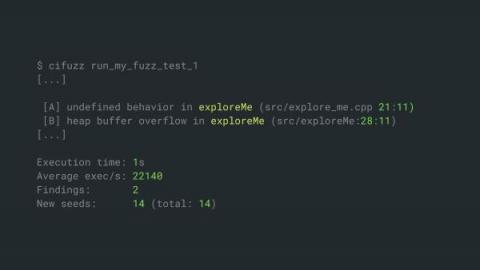
How to Simplify Fuzz Testing for C++
Today I want to show you a way to simplify fuzz testing for your C++ applications. If you read this article to the end, you will learn about an automated testing approach that can protect your applications against all sorts of memory corruptions and other security vulnerabilities.
The Myths and Truths of Employee Monitoring
Early in the pandemic, searches related to “how to monitor employees working from home” increased by 1,705%. Without the oversight of managers in an office setting, many companies are concerned that their employees are less productive, and that there is an increase risk to the company. This is a major reason why the use of employee monitoring technology has soared in the past year.
Conquer the Three Battlegrounds of Modern Business Continuity and Disaster Recovery
One of the most empowering documents in an organization’s arsenal is its business continuity and disaster recovery (BCDR) plan. Sure, it lays out in detail everything bad that could happen to your business, but it also provides point-by-point strategies to respond to each of those threats. Or does it? A good BCDR plan is a living document that evolves alongside the threats its organization faces. The trouble is that the world is changing fast, and BCDR teams are breathlessly trying to keep up.
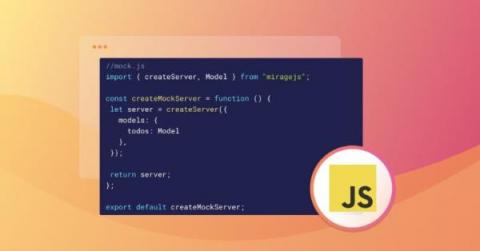
How to make a mock API server in JavaScript
Developing and testing a frontend feature can be difficult, especially when the backend it depends on is not ready. This dependency on a backend API often slows down the development process. In scenarios like this, developing a mock API can save you a lot of time by allowing you to develop your feature independent of the backend, and make it easier to test and identify scenarios where your API might fail before it is ready.
Archive Sidestepping: Self-Unlocking Password-Protected RAR
Trustwave SpiderLabs’ spam traps have identified an increase in threats packaged in password-protected archives with about 96% of these being spammed by the Emotet Botnet. In the first half of 2022, we identified password-protected ZIP files as the third most popular archive format used by cybercriminals to conceal malware.
Blockchain as a Service (BaaS)
A key share of growing technology is blockchain. Blockchain technology permits entities to share information quickly and firmly while not compromising on security. The engineering blockchain has hit the marketplaces everywhere nowadays. And it’s because blockchain has many applications that deliver higher output and reliability than the traditional network. Now that many businesses have begun to experiment with the blockchain, a full new sort of marketplace is developed.