Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Kintent® Launches World's First Free, Self-Service SOC 2 and NIST-CSF Readiness for Startups
Cyberattacks could worsen the global energy crisis
War, economic instability, external threats, and global politics affect the energy sector of a country or region. In addition, cyberattacks on critical infrastructure can cripple the strained energy market. Europe is facing a severe energy crisis, and European governments are getting prepared for this winter by managing the demands and keeping energy reserves. The EU (European Union) also accelerated the work to improve critical infrastructure defence and resilience.
What Airtel's new Face Match based eKYC Verification means for India
Airtel’s latest initiative prioritizes digital onboarding methods to assist online customer onboarding for its payments bank to create an account simply by doing a face match eKYC check on mobile devices. Airtel Payments Bank is the country’s first Payments Bank to offer this service, and it foreshadows India’s shift toward complete digital banking.
Risks Faced by Cloud-Native Apps and How to Assess Them
Modern organizations are adopting a cloud-native approach to their application development. While this approach provides many benefits, it also makes organizations face several challenges, including the challenge of securing the application with a completely different approach. In this blog, we will discuss how software changes and how organizations should think about securing it.
Join Us in Making History: Free SOC 2 Readiness for Startups
Compliance software platforms have been around since 2016. These solutions may vary in focus, but typically, they share the same few traits. They tend to prioritize speed over quality, hide their pricing structures, and don’t allow prospects to try out the product until they’ve officially run through a demo and signed a contract.
Unlock any CLI using biometrics with 1Password Shell Plugins
1Password Shell Plugins brings the security and ease of use of biometrics to every tool in your terminal.
Four Elements Security Leaders Must Consider When Building an Autonomous SOC
The SOC is changing. And to keep cybercriminals from wreaking havoc, security teams must mature their security operations to derive more value from the systems, tools, and data at their disposal. To do so, organizations are increasingly automating more SOC tasks and have long-term plans to build autonomous SOCs to augment their security analysts.
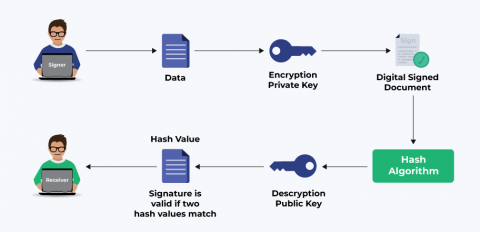
What are the Differences Between Encryption and Signing? Why Should You Use Digital Signatures?
While we have all used digital security certificates like SSL/TLS, code signing certificates, or others, many don’t know the security technology behind them. Stringent security standards ensure that the cyber threats looming around us never get to our digital systems. Due to such threats, there’s a constant advancement happening in data security technology to protect sensitive information. Encryption and Signing are two methods used widely for data security.
Hackers Are Using These 3 Techniques to Bypass MFA
There’s no denying that multi-factor authentication (MFA) is an essential security measure that significantly improves an organization’s cyber posture. However, there is no silver bullet in cybersecurity. Though multi-factor authentication proves extremely helpful, determined and resourceful cybercriminals can still find techniques to bypass it. Let’s look at some frequently-used methods cyber-attackers leverage to bypass MFA.