Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
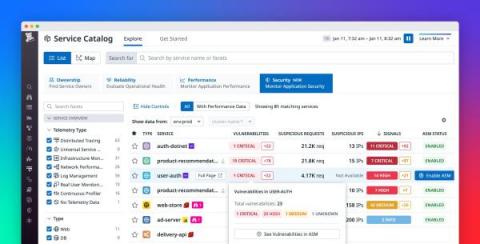
Gain visibility into risks, vulnerabilities, and attacks with APM Security View
As your business grows and your services scale in number and complexity, it’s difficult to maintain a rapid pace of innovation while keeping your applications secure. It’s particularly challenging to respond to attacks, as DevOps and security teams need to collaborate to understand each attack’s root cause and remediate the vulnerabilities that enabled it.
Accelerating Secure Infrastructure Deployments with Policy-as-Code Authorization
Styra is today introducing a better way for platform engineering teams to empower hundreds or thousands of developers and accelerate their infrastructure deployments, including the broadest policy library and infrastructure authorization toolset for Kubernetes, Terraform and CloudFormation.
Proven Ways to Boost Your Web Application Security in 2023
Several web applications have been booming in recent years, as every organization prefers it for business due to its easy maintenance and advanced features. And it’s evident that when a firm uses any application, it processes confidential data. Whenever data comes into play, cyber-attacks and security aspects accompany it. And same is the case with web applications. Like other software, application security is also crucial for web applications.
How IT Teams Can Protect Their Organization's Social Media Accounts
Social media managers play a pivotal part in enabling brands to raise awareness and connect with customers online. In that role, they sift through irrelevant and sometimes offensive content to provide prompt support and accurate information on popular platforms like Tik Tok, Twitter, Instagram, LinkedIn and Facebook. Social media is a common entry point for cybercriminals looking to get inside an organization.
The Limitations of Endpoint Detection and Response (EDR)
How Cross-Site Scripting (XSS) Attacks Work & How To Prevent Them
Cross-Site Scripting (XSS) attacks are bad news. And they can affect lots of people, often unknowingly. Chief among the top cybersecurity threats affecting users worldwide, any website with unsafe elements can become vulnerable to XSS attacks — making visitors to that website unwitting cyberattack victims. To secure your website from XSS attacks, you must first know what they are.
SIEM Systems for IBM AS400
Security Information and Event Management (SIEM) systems are essential for protecting IBM AS400 systems in the financial industry. These systems are designed to collect, analyze and correlate log data from various sources, including servers, network devices, and applications, to identify security threats and compliance violations.
Top Five Cybersecurity Pain Points of 2023 - Internet Trends Analysis
According to an analysis realized on millions of comments and posts from technical communities and forums on the internet, these are currently the biggest cybersecurity needs or pain points that are lacking solutions or improvement across organizations: It’s worth noting that the above-mentioned concerns can vary by organization size, industry, and specific use case, but they are the common pain points that are frequently mentioned in the online communities and forums.
Advanced persistent threats (APTs) Prevention with SIEM Systems
Advanced persistent threats (APTs) and targeted attacks are a growing concern for organizations of all sizes. These types of cyber attacks are characterized by their high level of sophistication and the ability to evade traditional security measures. In order to defend against APTs, organizations need to adopt a multi-layered approach that includes implementing security information and event management (SIEM) systems.