Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Top 10 Blockchain Auditing Companies
The blockchain industry is expected to grow and hit a value of $163 billion by 2029. With such growth will also come the ever-increasing need for ensuring the protection of blockchain applications. In comes blockchain auditing companies.
CrowdStrike and Dell: Making Cybersecurity Fast and Frictionless
Cybersecurity is often about making progress: Progress in the way organizations procure, deploy and manage software; in the new skills and techniques teams acquire to run their cybersecurity programs; and in stopping breaches to protect hard-earned productivity gains.
CrowdStrike's Artificial Intelligence Tooling Uses Similarity Search to Analyze Script-Based Malware Attack Techniques
According to the AV-TEST Institute, more than 1 billion strains of malware have been created, and more than 500,00 new pieces of malware are detected every day. One of the main reasons for this rapid growth is that malware creators frequently reuse source code. They modify existing malware to meet the specific objectives of an attack campaign or to avoid signature-based detection.
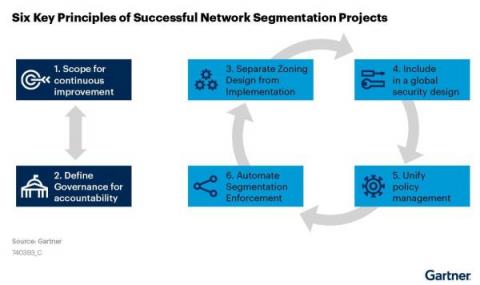
Asset Visibility and Behavior: The Keys to Segmentation Success
Recently, Gartner® refreshed one of its foundational cybersecurity research, “The 6 Principles of Successful Network Segmentation Strategies.”1 The principles covered in the research are tried and true. Segmenting networks to improve security and performance is nothing new to security teams, yet the same challenges persist year after year.
ITIL For Change Management and Continuous Improvement - Powered by Tripwire
During discussions with clients about their approach to managing IT services, many organizations refer to the Information Technology Infrastructure Library (ITIL) practices as a key component of their approach. This is not surprising, as the ITIL framework provides a practical methodology for IT management, enabling the use of technology to align with business needs.
Europe's transport sector terrorised by ransomware, data theft, and denial-of-service attacks
A new report from ENISA, the European Union Agency for Cybersecurity, looking at cyberattacks targeting the European transport network over a period of almost two years, has identified that ransomware has become the prominent threat. ENISA's report, its first ever analysis of the myriad of cybersecurity threats facing the transport sector in the EU, mapped and studied cyber incidents targeting aviation, maritime, railway, and road transport between January 2021 and October 2022.
Value Over Growth: How Tech Leaders Can Streamline IT Operations
More prudent use of endpoint management tools could hold the key.
The Shift to the Cloud and its Implications for Application Security
Everybody’s doing it: shifting applications to the cloud. More flexibility. More storage. More scalability. But how does this affect application security? What challenges does it present?
BlackGuard stealer extends its capabilities in new variant
AT&T Alien Labs researchers have discovered a new variant of BlackGuard stealer in the wild, infecting using spear phishing attacks. The malware evolved since its previous variant and now arrives with new capabilities.