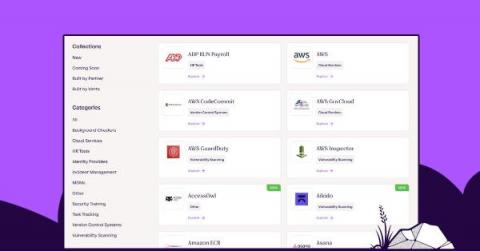
Vanta delivers over 50 new integrations in one quarter
We’re thrilled to announce that we’ve delivered more than 50 new system integrations over the past quarter, taking us to a total of 110 integrations. This is far ahead of any other automated compliance solution in the market, reflecting our innovation velocity and long-term commitment to ensuring customer value and success with Vanta.