How to Enable Logging: Secure Cloud-native Development Series
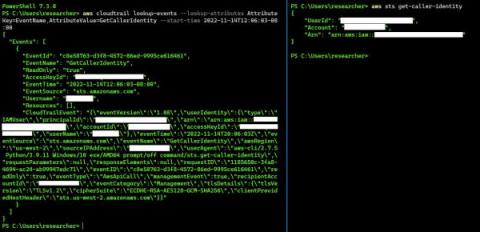
Build secure cloud-native applications by avoiding the top five security pitfalls we lay out in our Secure Cloud-native Development Series. This blog is the second part of the series, and it will teach you how and why to enable logging from the start. We’re going to talk about enabling logging (cloud logging, to be specific). What’s the difference? Not much, other than the fact that it’s another managed service integrated with the tools we should already be utilizing.