Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
CyberArk Named a Leader in the Gartner Magic Quadrant for PAM for the Fifth Time
Today, I’m honored to share that CyberArk has been named a Leader in the “2023 Gartner® Magic Quadrant™ for Privileged Access Management.” This is the fifth time our company has been positioned as a Leader in this report.
How to avoid web cache poisoning attacks
Web cache poisoning is a cyber attack that wreaks havoc on unsuspecting websites. It exploits vulnerabilities by caching mechanisms that web servers, proxies, and content delivery networks (CDNs) use, compromising data integrity. Malicious actors can use cache poisoning to deliver malicious payloads, tamper with sensitive information, or redirect users to fraudulent websites. In this article, we’ll comprehensively explore web cache poisoning attacks and how they work.
Breaking the Barrier of Dynamic Testing: Detect and Autoconfigure Entry Points With CI Spark
How to Solve the Cloud vs On-Premise Security Dilemma
Organizations need to protect themselves from the risks of running their business over the internet and processing sensitive data in the cloud. The growth of SaaS applications, Shadow IT and work from anywhere have therefore driven a rapid adoption of cloud-delivered cybersecurity services. Gartner defined SSE as a collection of cloud-delivered security functions: SWG, CASB, DLP and ZTNA. SSE solutions help to move branch security to the cloud in a flexible, cost-effective and easy-to-manage way.
CIO Vs. CISO: Who Does What?
The SEC's New Cybersecurity Regulations Part II: What Shareholders Should Know
Chapter 1: Android Malware Starters Pack
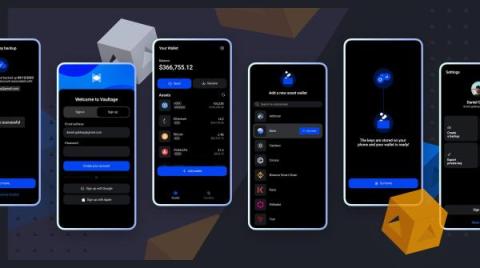
Introducing Fireblocks Non-Custodial Wallets-As-A-Service
Fireblocks introduces its non-custodial wallet-as-a-service (WaaS) offering built for brands, corporates, fintechs, and Web3 businesses. Fireblocks’ non-custodial wallets (NCW) are the first of their kind to offer multi-layer, defense-in-depth security alongside industry-leading customization options and scalability.
Netskope Threat Labs Stats for August 2023
Netskope Threat Labs publishes a monthly summary blog post of the top threats we are tracking on the Netskope platform. The purpose of this post is to provide strategic, actionable intelligence on active threats against enterprise users worldwide.