Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Improve visibility and identify risk across your Google Cloud environments with AlgoSec CloudFlow
With expertise in data management, search algorithms, and AI, Google has created a cloud platform that excels in both performance and efficiency. The advanced machine learning, global infrastructure, and comprehensive suite of services available in Google Cloud demonstrates Google’s commitment to innovation. Many companies are leveraging these capabilities to explore new possibilities and achieve remarkable outcomes in the cloud.
Why Reduce Software Supply Chain Risks with Intelligent Software Security
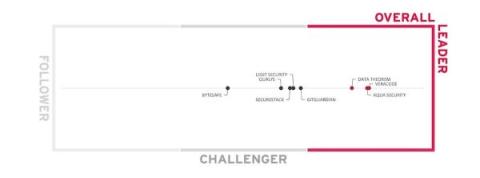
There’s a growing array of risks lurking within the supply chain of the digital solutions we increasingly depend upon. Leaving gaps in your software supply chain security (SSCS) could spell disaster for your organization. Let’s explore how new analysis defines an end-to-end solution and why Veracode was ranked as an Overall Leader, Product Leader, Innovation Leader, and Market Leader in the Software Supply Chain Security Leadership Compass 2023 by KuppingerCole Analysts AG.
Falcon Complete for Service Providers: New Program Expands Access to Market-Leading MDR Service
CrowdStrike is expanding access to its market-leading managed detection and response (MDR) service, CrowdStrike Falcon® Complete. With the announcement of Falcon Complete for Service Providers, CrowdStrike partners can now license and build upon Falcon Complete to provide 24/7 expertise to customers, empowering them to augment their cybersecurity teams and stop breaches.
Using a Standardized Approach for Measuring Cybersecurity in Government
Last week at the annual Billington CyberSecurity Summit in Washington, DC, officials from government agencies gathered with industry leaders to discuss cyber threats, as well as geopolitics and issues of national security. One of the highlights was a fireside chat on Friday with Anne Neuberger, deputy national security adviser for cyber and emerging technology.
Product Quality at Rubrik - Part 1
At Rubrik, we are on a mission to Secure the World’s Data and we consider product quality a top priority. In this blog, we will talk about the automated test strategy we follow at Rubrik to ensure the best quality products for our customers. Before we deep dive into our test strategy and the process we follow, let’s quickly understand what product quality means and why it’s important to our organization as well as our customers.
How Software Supply Chain Security Regulation Will Develop, and What Will It Look Like?
The escalation of international legislative interest in regulating the software supply chain has led to an increasing likelihood that tools such as software bills of materials (SBOMs) and AppSec solutions will become essential for companies doing business in the public sector or in highly regulated industries. However, the process of building and enforcing effective regulations presents challenges as well.
Comply with India's Digital Personal Data Protection Act using Endpoint Central
Many countries across the globe are realizing the importance of the right to privacy in the digital era. The GDPR, the data privacy legislation for the European Union, came into force in 2018 and became the guiding star for an array of privacy laws. The Digital Personal Data Protection Act (DPDPA) by the Indian government is the latest privacy law aimed at protecting individuals’ privacy while ensuring hassle-free business operations.
Fireblocks Launches Industry's Most Secure Non-Custodial Wallet Built for Fintechs & Corporates in Web3
Microsoft Teams Phishing Campaign Distributes DarkGate Malware
Researchers at Truesec are tracking a phishing campaign that’s distributing the DarkGate Loader malware via external Microsoft Teams messages. “On August 29, in the timespan from 11:25 to 12:25 UTC, Microsoft Teams chat messages were sent from two external Office 365 accounts compromised prior to the campaign,” the researchers write.