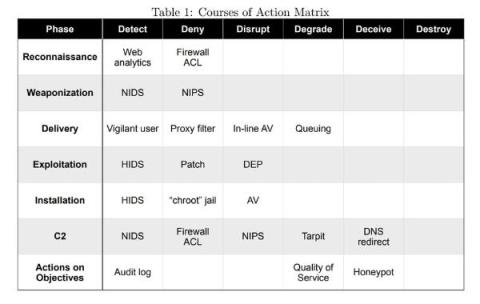
How Does the Kill Chain Apply to Network-Derived Evidence?
When Eric M. Hutchins, Michael J. Cloppert, and Rohan M. Amin published their paper “Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains” in late 2010, they changed the way security personnel thought about defending their digital assets. The paper continues to be a useful model for defense today. This article proposes ways that modern network-derived evidence applies to the kill chain.