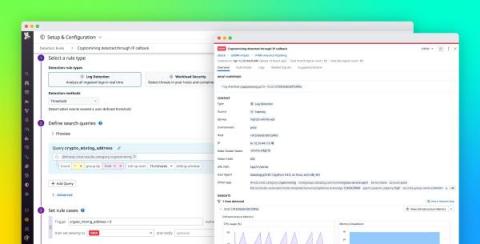
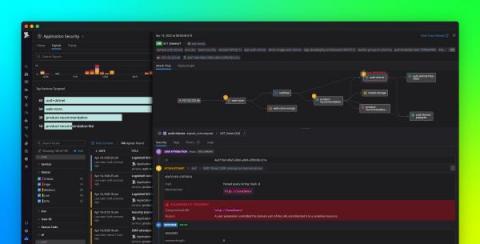
5 Vulnerability Assessment Scanning Tools: 5 Solutions Compared
Vulnerability assessments define, identify, classify, and prioritize flaws and vulnerabilities in applications, devices, and networks that can expose organizations, their products, services, code, and applications, to attack. Security vulnerabilities allow malicious actors to exploit an organization’s applications and systems, so it is essential to identify and respond to them before attackers can exploit them.