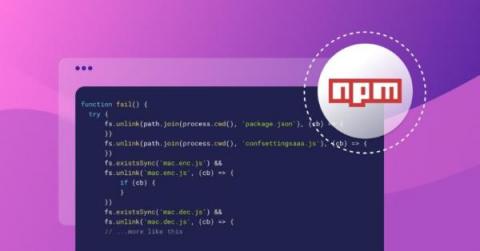
Where to store your 1Password Emergency Kit
In case of emergency – that is, forgetting your login for 1Password, or someone else needing to get in – the 1Password Emergency Kit can truly save the day. This short and sweet document keeps all the necessary details for getting into your account in one place. But you shouldn’t need to break glass to retrieve it (which is a huge pain to clean up, not to mention dangerous). Here’s how to keep your Emergency Kit both safe and accessible.