Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
The state of cloud-native security 2022 - Tigera's new market report
We are excited to announce the publication of our first State of Cloud-Native Security market report! The report compiles survey results from more than 300 security and IT professionals worldwide (all of whom have direct container responsibilities), and explores organizations’ needs and challenges when it comes to containers and cloud-native applications, specifically in the areas of security, observability, and compliance.
Reciprocity Community Edition Best Practices: How to Get Started with the Reciprocity ROAR Platform
Why Microsegmentation is Still a Go-To Network Security Strategy
Prof. Avishai Wool, AlgoSec co-founder and CTO, breaks down the truths and myths about micro-segmentation and how organizations can better secure their network before their next cyberattack.
NeoSystems Strengthens Channel Program; Names Kathlyn Gibbs to Lead Effort as VP, Partners and Alliances
TYSONS CORNER, Va., May 3, 2022 – NeoSystems, a full-service strategic outsourcer, IT systems integrator and managed services provider to the government contracting market, is strengthening its channel program and has named Kathy Gibbs to lead this effort as Vice President, Partners and Alliances.
What Is CSPM? A Closer Look at Cloud Security Posture Management
As we previously discussed in the Automating Your Cloud Security Posture Management (CSPM) Response blog post, CSPM is a vital component in any environment leveraging cloud services. Whether you are using a single cloud or are in a multi-cloud scenario, the complexity of these cloud platforms is constantly expanding. Staying on top of new changes in policies and functionality to ensure that you are maintaining a secure environment is daunting - and almost impossible to do without automation. No one has the resources to spend on maintaining a large team of cloud specialists who just audit everything that is in use.
Recapping Datadog Summit Denver 2022
After a two-year hiatus, Datadog customer summits are back. And what better place to begin in-person again than in sunny Denver, Colorado!
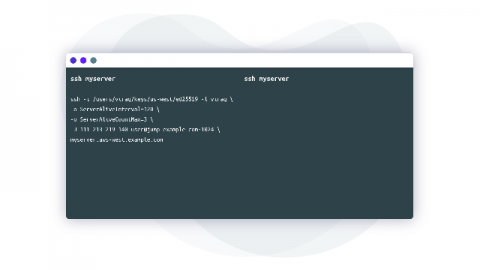
SSH configuration: ssh_config
This blog post covers some of my favorite settings for configuring the behavior of an ssh client (i.e. what is in the man pages for ssh_config). Whether you are looking to add some additional security constraints, minimize failures, or prevent carpal tunnel, ssh_config is an often underutilized, yet powerful tool. While the examples in this article focus on ssh configurations on unix based systems like linux and macOS, running an ssh server on windows is supported using openSSH.
Analysis on recent wiper attacks: examples and how wiper malware works
Wiper’s main objective is to destroy data from any storage device and make the information unavailable (T1485). There are two ways of removing files, logical and physical. Logical file removal is the most common way of erasing a file, performed by users daily when a file is sent to (and emptied from) the Recycle bin, or when it is removed with the command line or terminal with the commands del/rm.
What Is COBIT?
COBIT is an acronym for Control Objectives for Information and Related Technologies. The COBIT framework was created by Information Systems Audit and Control Association, ISACA to bridge the crucial gap between technical issues, business risks and control requirements. COBIT is an IT governance framework for businesses that want to implement, monitor and improve their IT management best practices.