Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
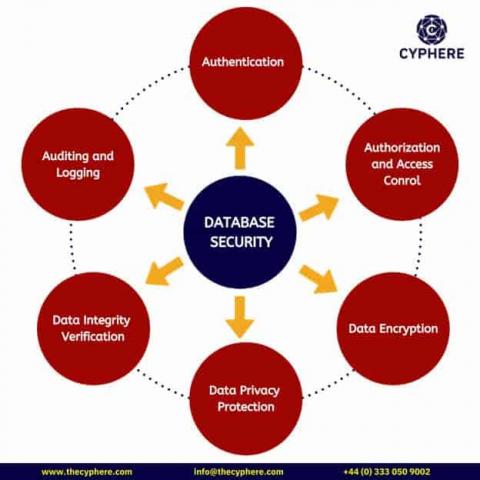
What is Database Security? Learn how to secure databases
Databases are essential for organisations because they store data critical for the organisation to function. This data can include customer information, financial records, and contact details. Organisations need to access this data quickly and securely to make decisions and run their business. A database can help them do this by providing a centralised location for all their data.
Calico workload-centric web application firewall (WAF): A better way to secure cloud-native applications
Container-based web applications built on microservices architecture, whether public-facing or internal, are critical to businesses. This new class of applications is commonly referred to as cloud-native applications. Read on to find out why traditional WAFs are no longer enough to protect cloud-native applications and how Calico’s new workload-centric WAF solves this problem.
How to Create and Deploy a Content Security Policy
When it comes to client-side security, creating and deploying a content security policy (CSP) can serve as a solid starting point. To deploy a content security policy, you must first identify assets, including first- and third-party resources that will be loaded in the browser when a user visits your website. For those who haven’t heard of a content security policy (CSP), you probably know that it’s easier said than done. Let’s talk about what those steps are to deploy a CSP.
How to secure Kubernetes deployment with signature verification
When running containers in a Kubernetes cluster, trusting the images you deploy is key to enforce security. The use of mutable images represents a risk to the secure Kubernetes deployment and highlights the importance of having a reliable mechanism to ensure you run what you expect. In this blog, you will learn step-by-step how to implement a secure Kubernetes deployment.
The security course missing from higher education
Have you ever looked at the curriculum offered in a Computer Science program? Across many different universities, there are some commonalities among the courses students take. Generally, there’s an introductory course in the first semester that introduces students to the world of computer science. Then over the course of subsequent semesters, students take courses about programming (including an introduction to OOP), databases, data structures, etc.
Top 7 Data Leak Detection Solutions
Today’s threat actors often carry out cyber attacks with the primary objective of accessing and exfiltrating sensitive information from your IT environment. Efforts to obtain this “crown jewel” information usually involve complex multi-phase cyber attacks. But another way in which sensitive data ends up in the hands of malicious actors with a lot less effort is when an organization exposes sensitive data assets in a data leak incident.
The Rise of Endpoint Security Risks: 6 Common Types
With flexible work environments now the norm, the use of endpoint devices has increased – whether your organization allows work-from-home days, hires freelancers, and collaborates through email and phone calls. Many employees require access to the corporate network to carry out their daily responsibilities, and endpoint devices allow employees to do just that. That said, endpoints have become one of the biggest attack vectors for cybercriminals since they are easier to target.
Ethics, Design and Cybersecurity
If you work in an organization, you’ve probably had to take a cybersecurity training course at some point during your time there. Regardless of whether you work in cybersecurity or not, most of us breeze through the slides or videos, halfway listening to the warnings about spear phishing emails and hacking tactics. We complete the training and then we tuck away the lessons learned until the next year when we have to do it all again.
The Role of Community in the Journey to the Autonomous SOC
No security team — at least no effective security team — can operate successfully in a silo. Even expert teams know the value of leveraging the power of the community to build effective security content, share intelligence, and keep current with best practices.