Are organizations taking outbound risk seriously enough?
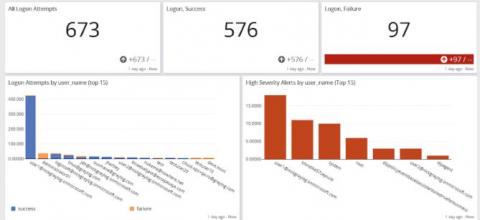
For many organizations, the rise of remote working brought on by the COVID-19 pandemic has significantly increased email communication. Our 2020 Outbound Email Security Report revealed that 94% of organizations experienced increased outbound email traffic due to remote working during the pandemic. This increase in outbound email traffic also increased outbound security risk. The report revealed that 93% of organizations suffered an outbound data breach in the same 12 months.