Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Bridging Network Security Gaps with Better Network Object Management
Prof. Avishai Wool, AlgoSec co-founder and CTO, stresses the importance of getting the often-overlooked function of managing network objects right, particularly in hybrid or multi-vendor environments.
Westcon-Comstor to add EfficientIP solution to its distribution portfolio in Europe, Africa and Asia-Pacific
Netacea Receives Top Score in Bot Detection Criterion in 2022 Analyst Report
Protecting your Microsoft 365 services against NOBELIUM attacks [E-book]
In December 2020, Microsoft came forward with details regarding what is now being considered the most extensive, severe cyberattack in history—the NOBELIUM attack. This shocking security breach by NOBELIUM, a group of Russian hackers, brought the cybersecurity world to a standstill with its well-planned and well-executed hacking. It compromised several organizations through a supply chain attack.
Data is Everywhere and Encryption Must Follow: Why You Need EDRM
It is becoming increasingly difficult to guarantee a safe boundary for your sensitive data. As work-from-anywhere cements, employees are now collaborating freely with each other, with contractors and with partners. But this freedom to collaborate more broadly also means information is being shared among devices, applications and networks that your organization doesn't necessarily have control over.
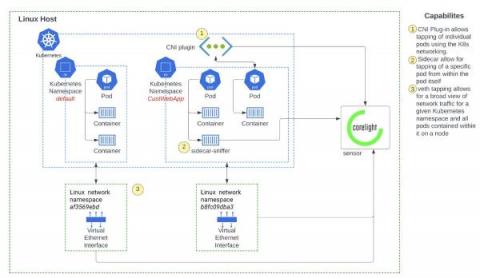
Deeper visibility into Kubernetes environments with network monitoring
Network monitoring solutions can overcome the security visibility blind spots in Kubernetes environments, by providing a source of truth for SOC analysts. Container security solutions broadly span the spectrum of (a) prevention - securing the container image and ensuring the right policies are in place during runtime and (b) detection - monitoring runtime events for threat detection and investigation.
What is data fabric and how does it impact Cybersecurity?
Amidst sweeping digital transformation across the globe, numerous organizations have been seeking a better way to manage data. Still in the beginning stages of adoption, data fabric provides many possibilities as an integrated layer that unifies data from across endpoints. A combination of factors has created a digital environment where data is stored in several places at once, leaving cracks in security for fraudsters to take advantage of.
How Y42 quickly onboards new team members with 1Password
Full-stack data platform Y42 is growing fast. The company kicked off 2021 with 15 employees. By February 2022, they were closing in on 100 team members.
The role of Threat Intelligence Platforms in Implementing Extended Detection and Response
As the new year continues to unfold, cybersecurity budget holders will be deep into the process of identifying where to allocate funds to best enhance protection against cyberthreats. The good news is that budgets are rising, with industry commentators frequently reporting that companies are committing more money to strengthening their posture against persistent and sophisticated threats.