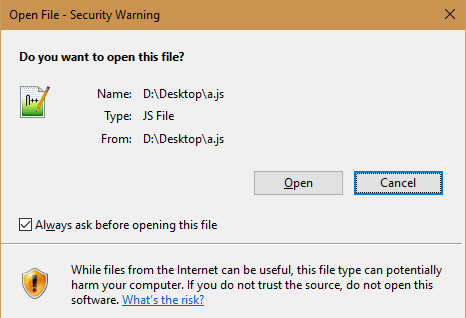
4 Ways Tech Companies Can Better Manage Vendor Risks in 2022
The technology industry is at the forefront of digital transformation, enabling all other industries to achieve greater operational capabilities and connectivity through innovative solutions. Tech companies, such as SaaS vendors, provide crucial software infrastructure to hundreds or even thousands of other organizations. These vendors access, store and transmit large volumes of sensitive information, including valuable healthcare and finance data.