Cyberthreat Trends in 2022H1: Threat Actors Observed, New Malware and Active Hacking Groups
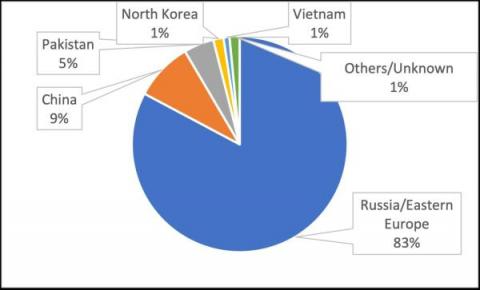
In our companion blog post, Vedere Labs analyzed the main ransomware trends we observed in the first half of 2022, including state-sponsored ransomware, new mainstream targets and evolving extortion techniques. Ransomware is the main threat targeting most organizations nowadays. However, three other notable cyberthreat trends also evolved during this period: Below we analyze each of these trends in more detail.