Who Should Be in Charge of Supply Chain Monitoring?
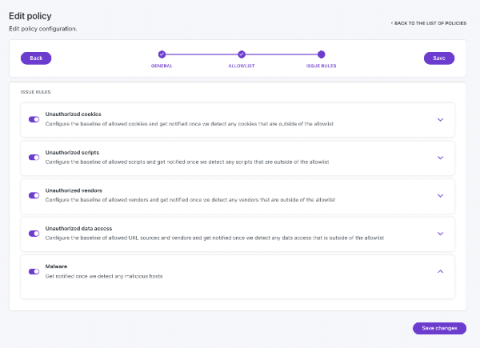
If you’ve paid attention to recent cybersecurity trends, you know that monitoring your supply chain is important due to the surge in supply chain attacks. But who, exactly, is responsible for that monitoring? Traditionally, the answer has been GRC (Governance, Risk and Compliance) teams, who monitor supply chains to help protect organizations against third-party risks.