Strategic Risk Management for CISOs: A Holistic and Consolidated Approach
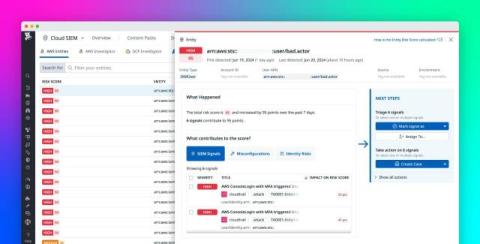
As Chief Information Security Officers (CISOs), it's crucial to manage risks in a holistic and consolidated manner as the landscape of threats, particularly those targeting applications, continues to evolve and expand. With the increasing reliance on digital technologies, artificial intelligence (AI), and cloud-based services, the attack surface for potential cyber threats is growing and changing.